Playing Chess with the Adversary: Value in Security Controls
Por um escritor misterioso
Last updated 20 maio 2024


DVIDS - News - JBB Chess Tournament tests decision-making skills

An Insider's Guide to the Active Adversary - Maxsum Consulting

That Time When People Thought Playing Chess Would Make You Violent

Navigating the Security Risks of Working with Third-Party Vendors and Contractors

PDF) Risk intelligence: a Centre for Risk Research discussion document
Astrology Game: What Chess Piece Owns The Moon - GaneshaSpeaks

Social Engineering Pen Testing

C-Suite Executives Shouldn't Leave Cybersecurity To CIOs And CISOs

US-China quantum rivalry creates harmful barriers to progress – Physics World

Game Theory and the Nuclear Game Against North Korea - Bloomberg

Your Guide to Objective-Based Penetration Testing

Tactical Cyber Intelligence by Intelligence and National Security Alliance - Issuu
Implement and Improve a Continuous Threat Exposure Management (CTEM) Program
Recomendado para você
-
 WE Games Best Value Tournament Chess Set, Green Board, Pieces, Bag, Instructions 78755135590120 maio 2024
WE Games Best Value Tournament Chess Set, Green Board, Pieces, Bag, Instructions 78755135590120 maio 2024 -
Chess Pieces Value - Openclipart20 maio 2024
-
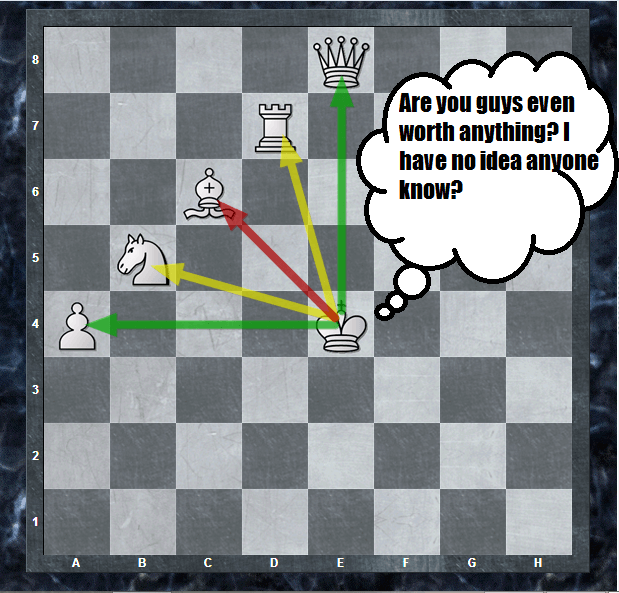 Chess Piece Relative Value20 maio 2024
Chess Piece Relative Value20 maio 2024 -
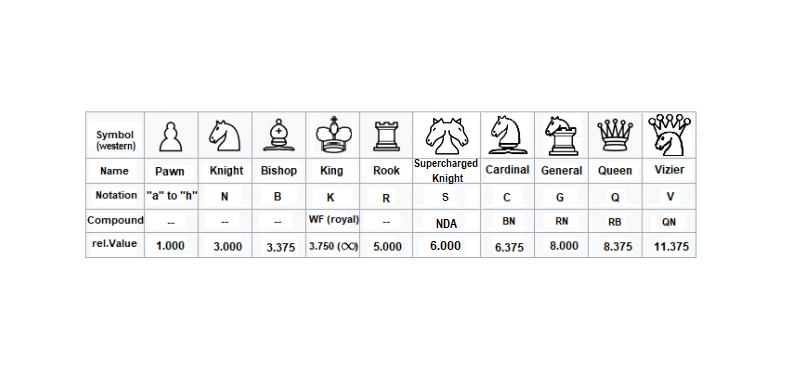 Exact relative value of chess pieces and fairy chess pieces20 maio 2024
Exact relative value of chess pieces and fairy chess pieces20 maio 2024 -
 Tip from the coach No. 4 Always be aware of your pieces value20 maio 2024
Tip from the coach No. 4 Always be aware of your pieces value20 maio 2024 -
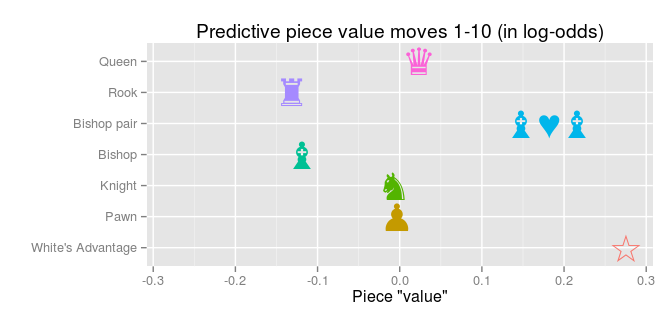 Big Data and Chess Follow-up: Predictive Piece Values Over the Course of a Game20 maio 2024
Big Data and Chess Follow-up: Predictive Piece Values Over the Course of a Game20 maio 2024 -
 Economy Chess Sets Value Chess Pieces - ChessBaron Chess Sets USA20 maio 2024
Economy Chess Sets Value Chess Pieces - ChessBaron Chess Sets USA20 maio 2024 -
 Chess Rules - Pieces Value - Chess Worksheet20 maio 2024
Chess Rules - Pieces Value - Chess Worksheet20 maio 2024 -
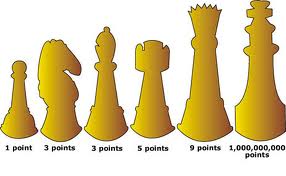 Value of the chess pieces « ChessManiac20 maio 2024
Value of the chess pieces « ChessManiac20 maio 2024 -
WE Games Best Value Tournament Chess Set, Black Board, Pieces, Bag, Instructions, 1 unit - Baker's20 maio 2024
você pode gostar
-
 Histórias da Bíblia - Livro de Atividades Infantil - Passatempos20 maio 2024
Histórias da Bíblia - Livro de Atividades Infantil - Passatempos20 maio 2024 -
Shingeki no kyojin: attack on titan End of the world, By Ataque A Los Titanes20 maio 2024
-
 Two Bedroom Granny Flat Design - Warilla20 maio 2024
Two Bedroom Granny Flat Design - Warilla20 maio 2024 -
 Best Gaming Channel Name,Trending, Famous, Gaming Name Suggestion for Channel and More in 202320 maio 2024
Best Gaming Channel Name,Trending, Famous, Gaming Name Suggestion for Channel and More in 202320 maio 2024 -
 One Piece ➺ Conis One piece pictures, Anime, Anime love20 maio 2024
One Piece ➺ Conis One piece pictures, Anime, Anime love20 maio 2024 -
 Notícias Otaku da Semana: 27 de setembro a 3 de outubro20 maio 2024
Notícias Otaku da Semana: 27 de setembro a 3 de outubro20 maio 2024 -
 Erros do Google Play em SAMSUNG Galaxy J7 Neo J701M20 maio 2024
Erros do Google Play em SAMSUNG Galaxy J7 Neo J701M20 maio 2024 -
 2D Jogo 9 Da Plataforma De Tileset Ilustração Stock - Ilustração20 maio 2024
2D Jogo 9 Da Plataforma De Tileset Ilustração Stock - Ilustração20 maio 2024 -
 111 1 Hora 1 a 120 maio 2024
111 1 Hora 1 a 120 maio 2024 -
 Play Free Girl Games Online20 maio 2024
Play Free Girl Games Online20 maio 2024

