Malware analysis Malicious activity
Por um escritor misterioso
Last updated 25 maio 2024

Malware Analysis Benefits Incident Response

How to Analyze Malware's Network Traffic in A Sandbox
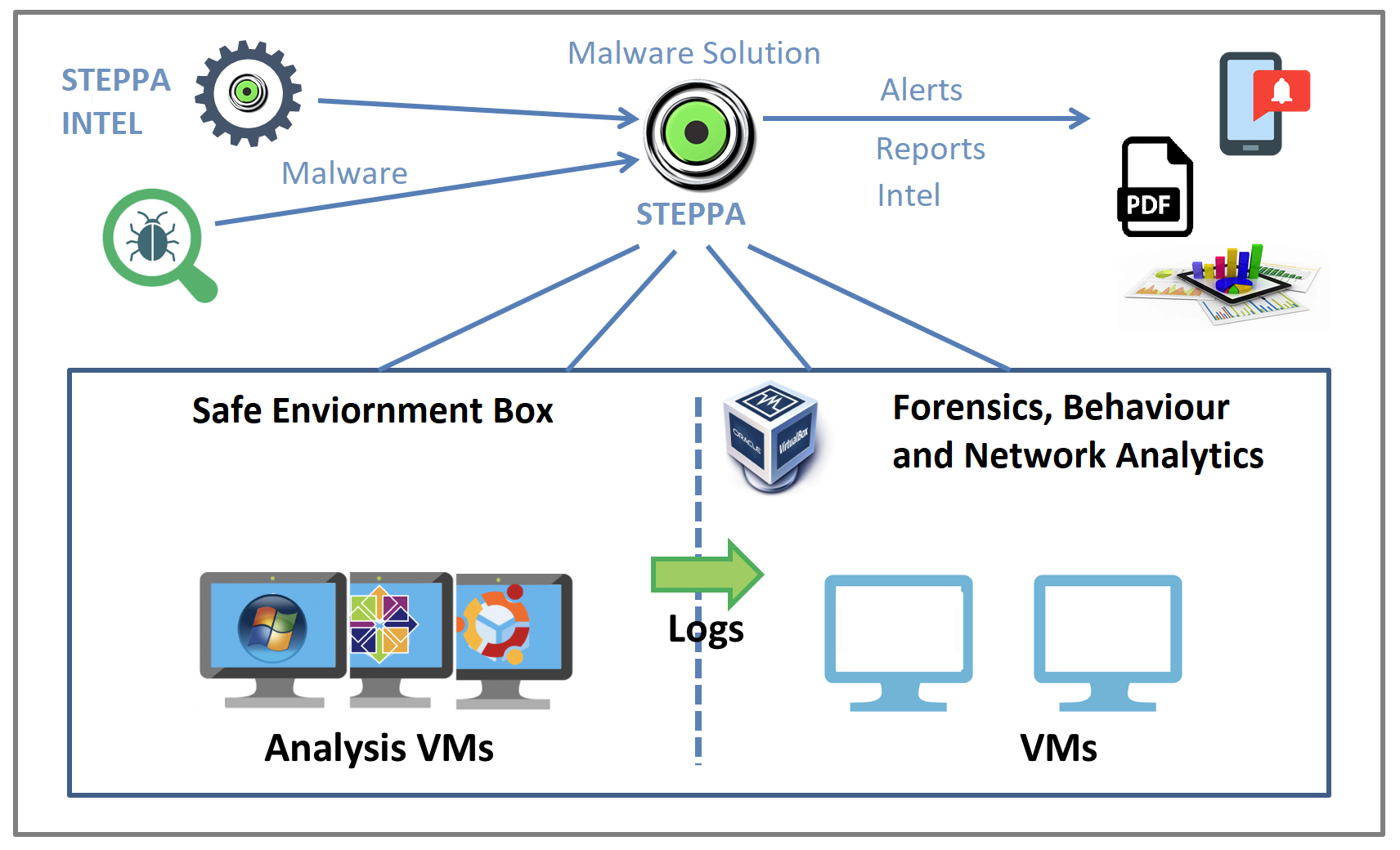
Malware Analysis Solution: Analyze, Detect, and Protect

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1 · Arch Cloud Labs
Malware analysis CQChallenge5.zip Malicious activity

TryHackMe Hacktivities

Malware Analysis: Steps & Examples - CrowdStrike

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging Rhysida ransomware targeting critical sectors - Industrial Cyber
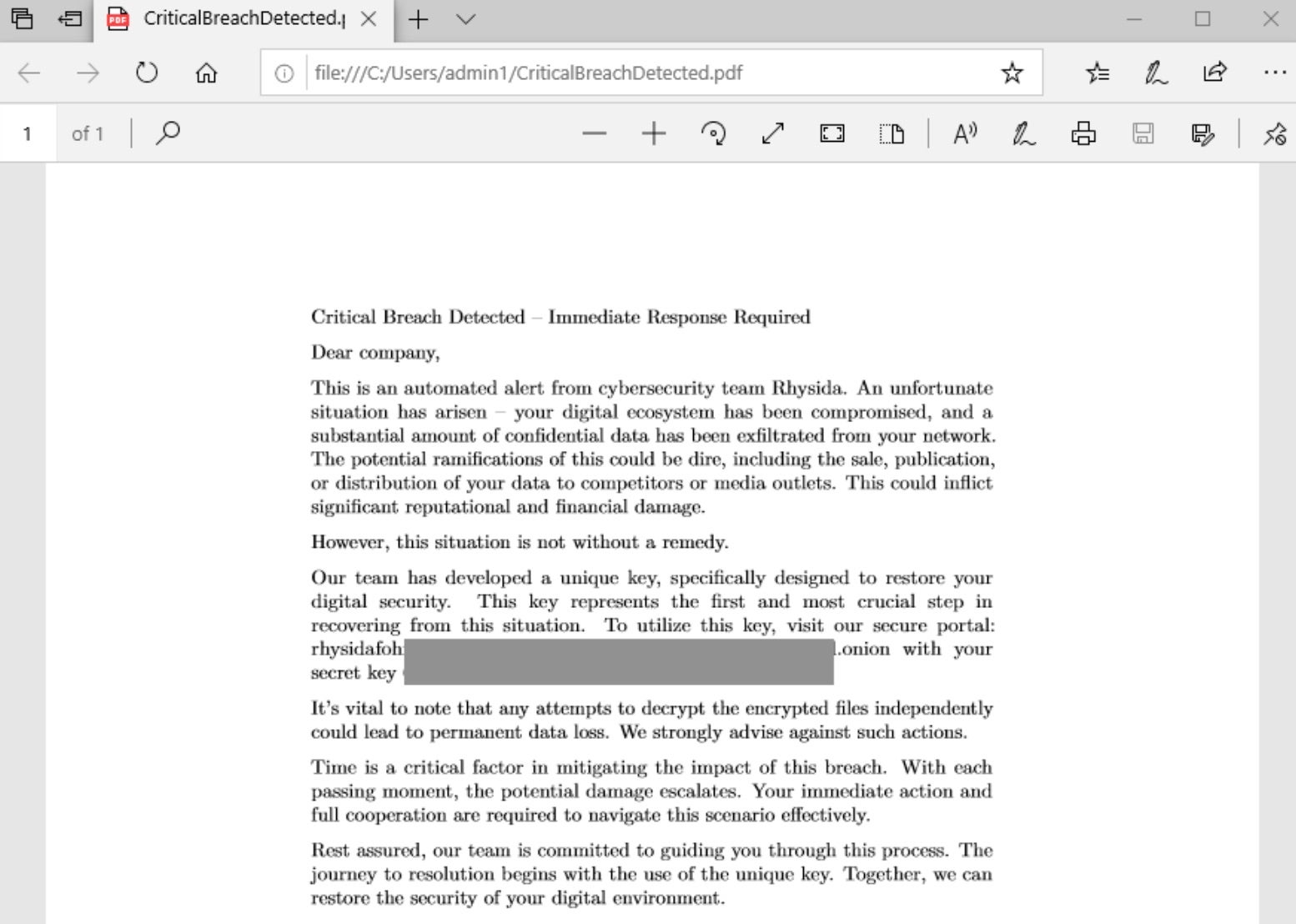
Rhysida - SentinelOne

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable

Dynamic malware analysis [34]

Malware Analysis: Steps & Examples - CrowdStrike
Recomendado para você
-
ipchicken.com Traffic Analytics, Ranking Stats & Tech Stack25 maio 2024
-
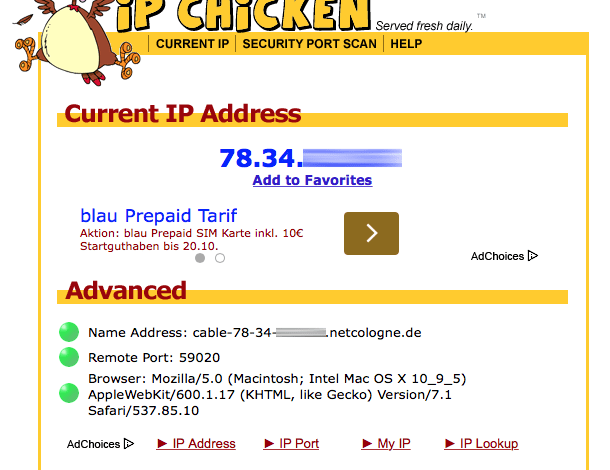 Read own IP address and check anonymization25 maio 2024
Read own IP address and check anonymization25 maio 2024 -
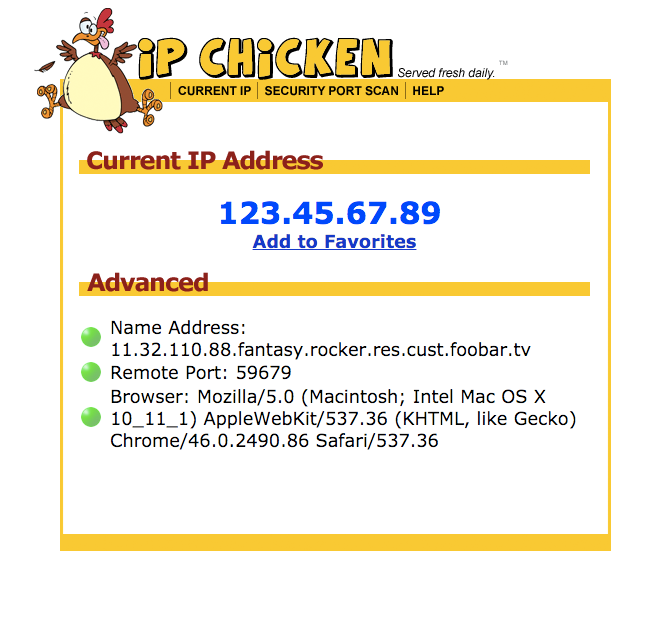 Show Your Public IP - Restreamer25 maio 2024
Show Your Public IP - Restreamer25 maio 2024 -
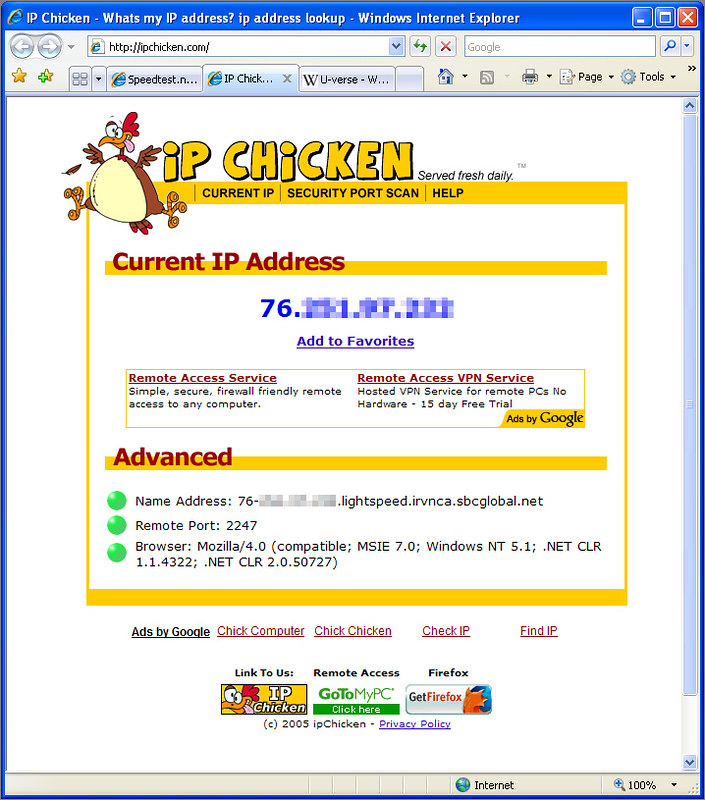 IPChicken, Woo hoo! Lightspeed!, Richard De Guzman25 maio 2024
IPChicken, Woo hoo! Lightspeed!, Richard De Guzman25 maio 2024 -
 ipchicken|TikTok Search25 maio 2024
ipchicken|TikTok Search25 maio 2024 -
 Ina Paarman Chicken Stock Powder 150g – African Breese25 maio 2024
Ina Paarman Chicken Stock Powder 150g – African Breese25 maio 2024 -
 Honey Garlic Chicken using Instant Pot - My DairyFree GlutenFree Life25 maio 2024
Honey Garlic Chicken using Instant Pot - My DairyFree GlutenFree Life25 maio 2024 -
 ipchickenhawk.com - What is my IP Address - whatsm - IP Chickenhawk25 maio 2024
ipchickenhawk.com - What is my IP Address - whatsm - IP Chickenhawk25 maio 2024 -
:max_bytes(150000):strip_icc()/whats-my-ip-google-0c2db49dfa084c26a9806f42234a612e.png) How to Find Your IP Address in Windows25 maio 2024
How to Find Your IP Address in Windows25 maio 2024 -
 Delicious Chicken Tortellini Skewers - An Easy, Healthy Meal - Just Plain Cooking25 maio 2024
Delicious Chicken Tortellini Skewers - An Easy, Healthy Meal - Just Plain Cooking25 maio 2024
você pode gostar
-
 The Pool Parties of South Beach Miami - Travel Deeper with Gareth Leonard25 maio 2024
The Pool Parties of South Beach Miami - Travel Deeper with Gareth Leonard25 maio 2024 -
 Finally got a rare race after 3650 robux. : r/deepwoken25 maio 2024
Finally got a rare race after 3650 robux. : r/deepwoken25 maio 2024 -
 DVD ANIME WORLD'S End Harem: After World *UNCENSORED* Vol.1-11 END English Subs $38.67 - PicClick AU25 maio 2024
DVD ANIME WORLD'S End Harem: After World *UNCENSORED* Vol.1-11 END English Subs $38.67 - PicClick AU25 maio 2024 -
 Sonic.exe Part 3: Dr. Eggman Checks Out (FINALE)25 maio 2024
Sonic.exe Part 3: Dr. Eggman Checks Out (FINALE)25 maio 2024 -
 Pokémon Brilliant Diamond & Pearl Double Pk c/ Steelbook - Switch - Game Games - Loja de Games Online25 maio 2024
Pokémon Brilliant Diamond & Pearl Double Pk c/ Steelbook - Switch - Game Games - Loja de Games Online25 maio 2024 -
 Adivinha o país pela Bandeira, Quiz sobre Bandeiras25 maio 2024
Adivinha o país pela Bandeira, Quiz sobre Bandeiras25 maio 2024 -
 RollerCoaster Tycoon World25 maio 2024
RollerCoaster Tycoon World25 maio 2024 -
 Jogue Plants vs. Zombies Garden Warfare 2 de graça por tempo limitado25 maio 2024
Jogue Plants vs. Zombies Garden Warfare 2 de graça por tempo limitado25 maio 2024 -
 Pokémon TCG: M Charizard EX (69/106) - XY2 Flash de Fogo em25 maio 2024
Pokémon TCG: M Charizard EX (69/106) - XY2 Flash de Fogo em25 maio 2024 -
Topo de bolo personalizado, tema: Maquiagem25 maio 2024
