Malware analysis Malicious activity
Por um escritor misterioso
Last updated 23 maio 2024
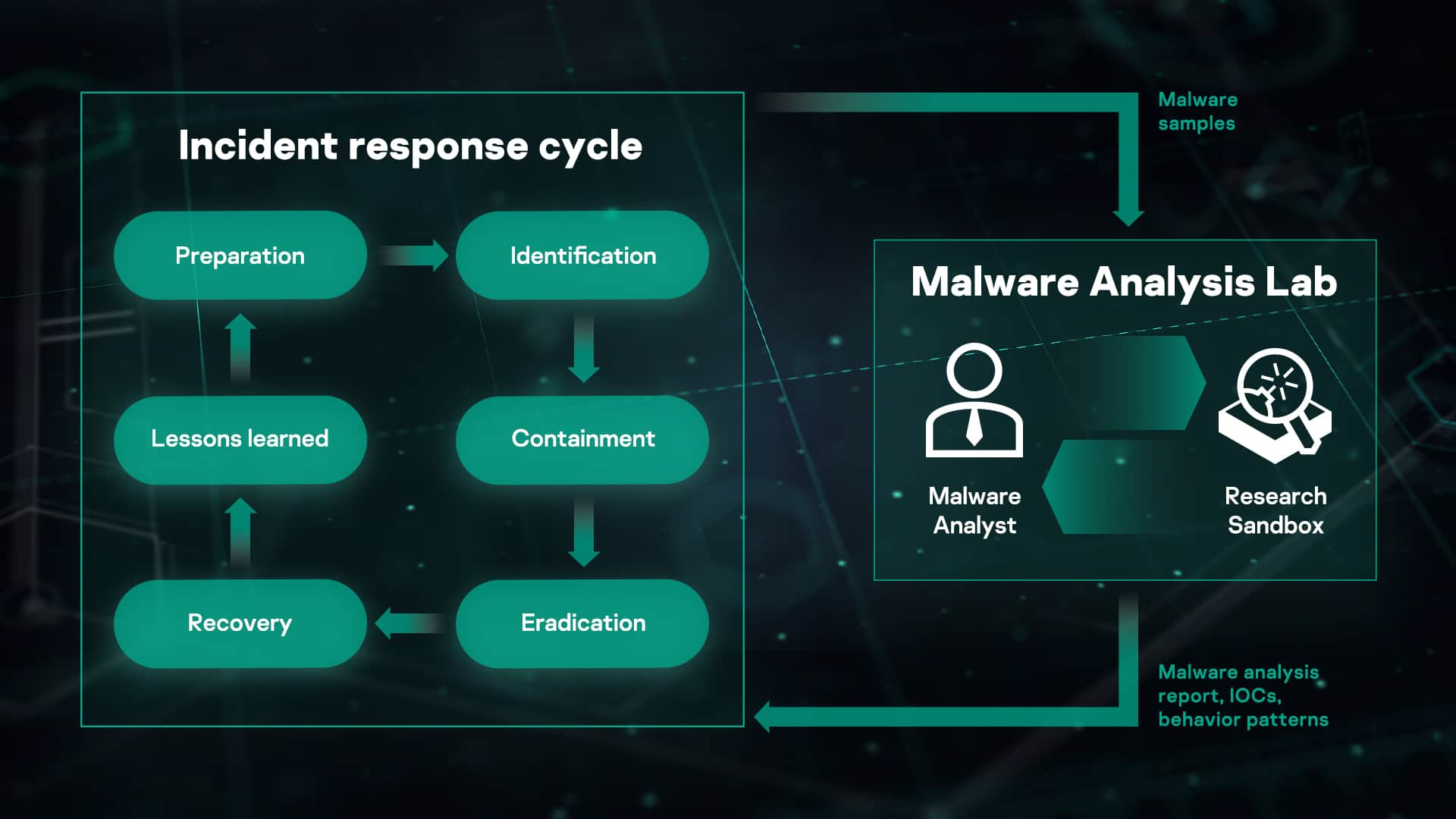
Advanced Automated Malware Analysis – Kaspersky Research Sandbox

AlienVault - Open Threat Exchange
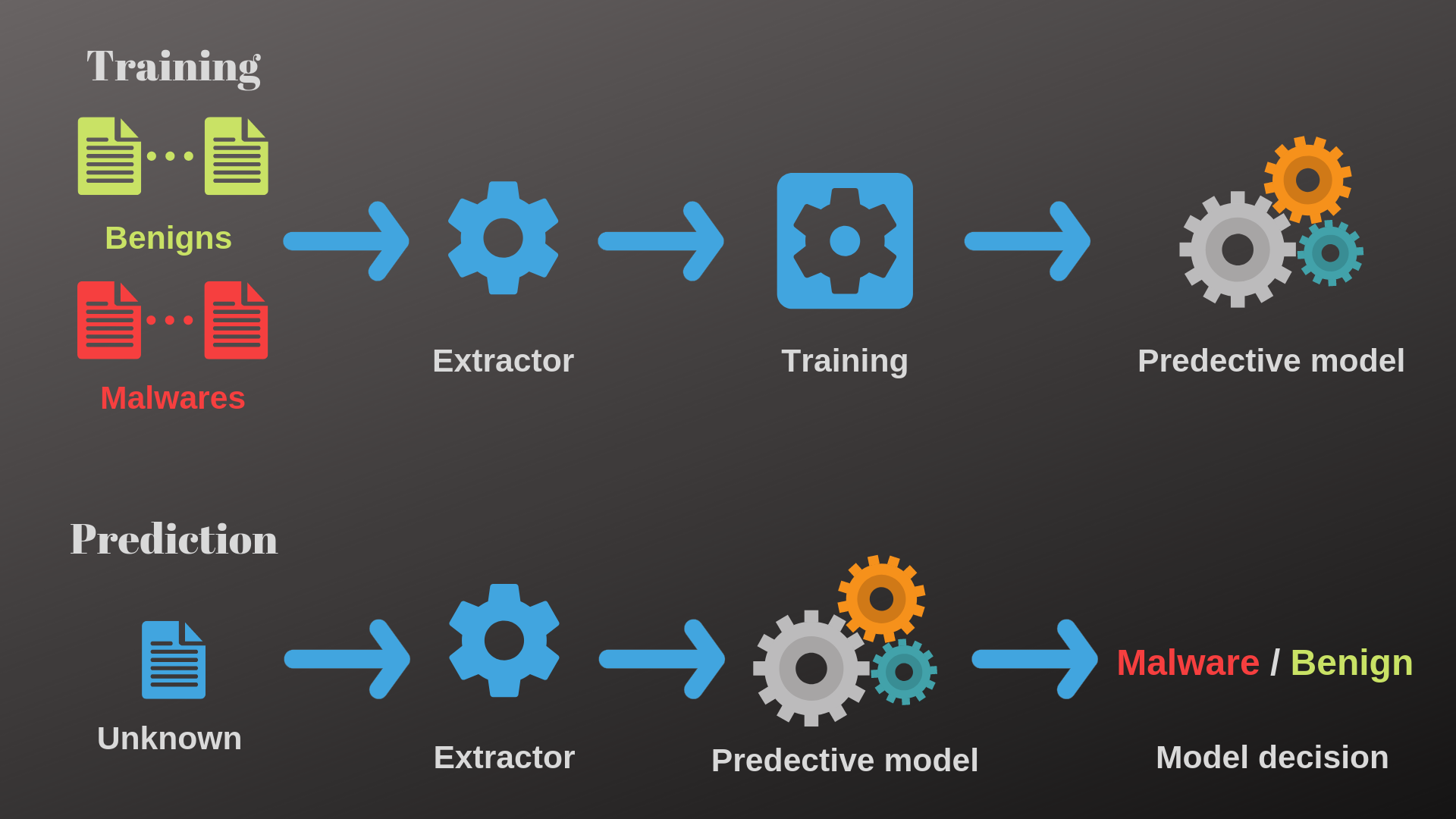
Feature Extraction and Detection of Malwares Using Machine Learning
Malware analysis index.html Malicious activity

Patch Now: Exploit Activity Mounts for Dangerous Apache Struts 2 Bug

Malware analysis file Malicious activity
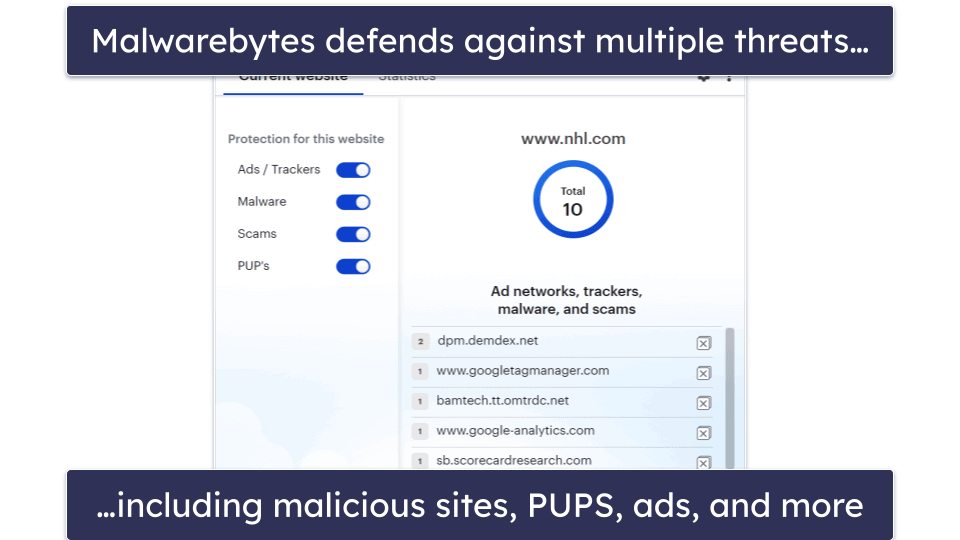
10 Best (REALLY FREE) Antivirus Software for Windows in 2023

Malware Analysis: Steps & Examples - CrowdStrike

A detailed analysis of the Menorah malware used by APT34

Malware analysis index.html Malicious activity

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen
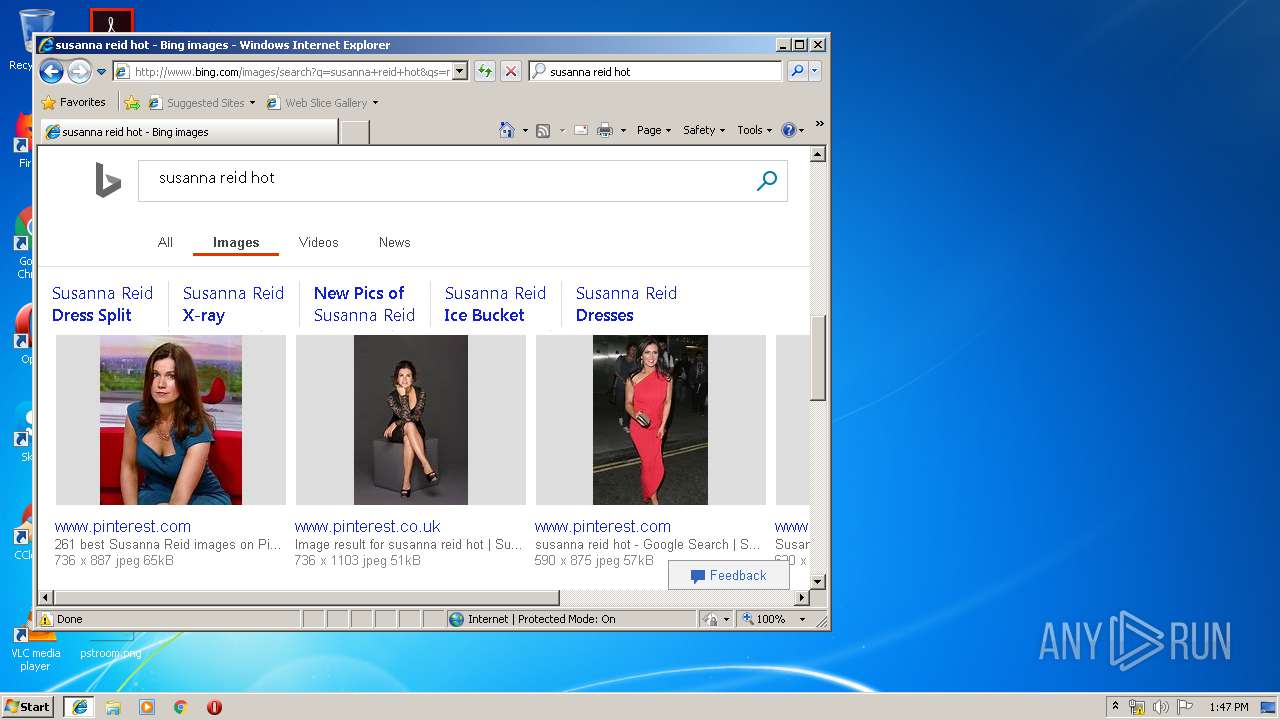
Malware analysis index.html Malicious activity

MetaDefender Cloud Advanced threat prevention and detection
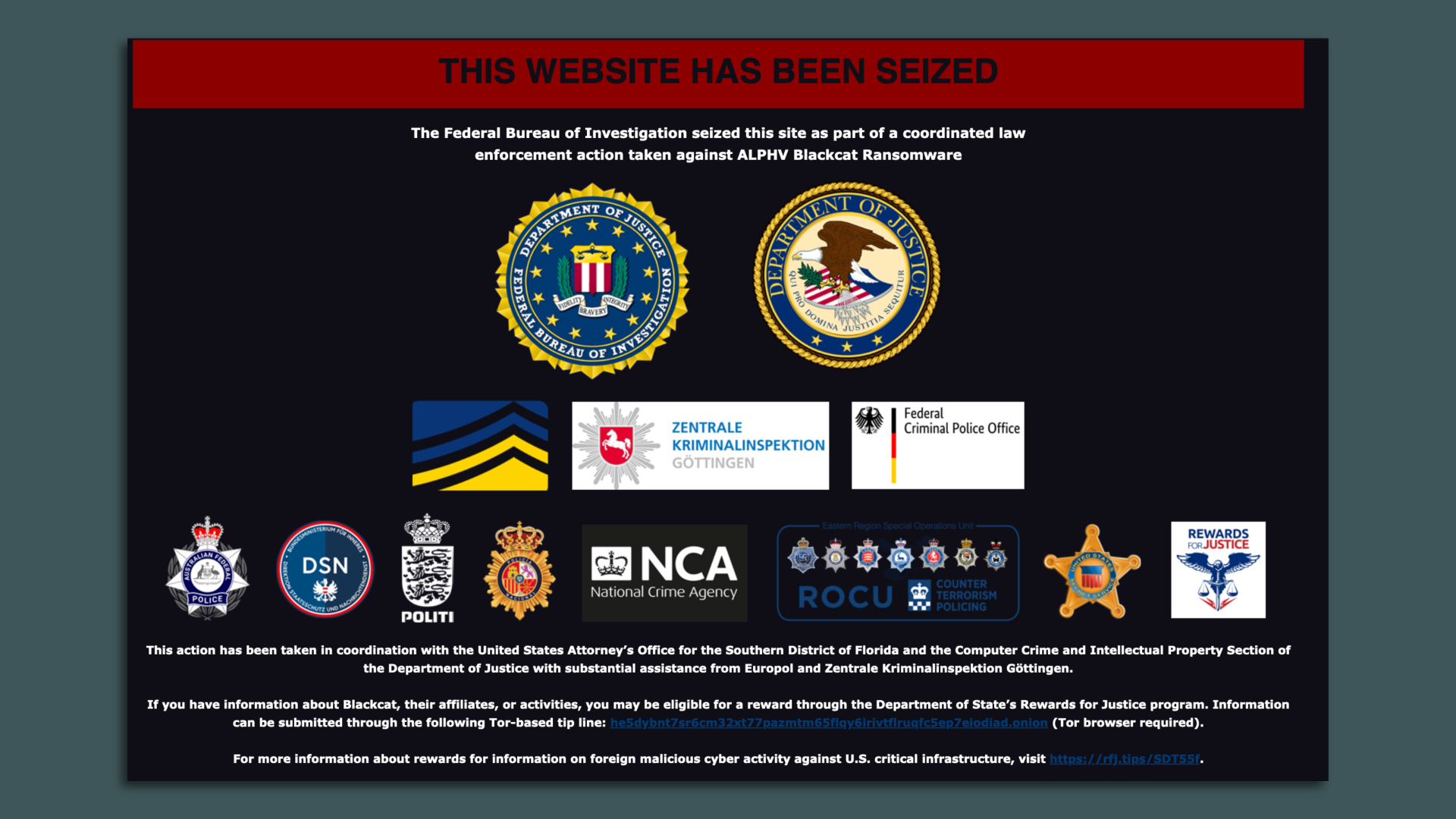
U.S. law enforcement seizes BlackCat ransomware site, distributes decryption key

Malware Analysis: Steps & Examples - CrowdStrike
Recomendado para você
-
Roblox Condo Disboard23 maio 2024
-
Reserved Condo - Roblox23 maio 2024
-
 Roblox Condo Games: Emma's Gamer Girl Journey23 maio 2024
Roblox Condo Games: Emma's Gamer Girl Journey23 maio 2024 -
 Cat Condo - Download23 maio 2024
Cat Condo - Download23 maio 2024 -
Discover - Roblox23 maio 2024
-
 Roblox Condo Map New23 maio 2024
Roblox Condo Map New23 maio 2024 -
 Blog - Roblox Condos23 maio 2024
Blog - Roblox Condos23 maio 2024 -
 EXPOSING Secret Condo Games on Roblox!23 maio 2024
EXPOSING Secret Condo Games on Roblox!23 maio 2024 -
 Super Monsters Ate My Condo! for iPhone - Download23 maio 2024
Super Monsters Ate My Condo! for iPhone - Download23 maio 2024 -
 Download Sylvie from Fortnite for GTA San Andreas23 maio 2024
Download Sylvie from Fortnite for GTA San Andreas23 maio 2024
você pode gostar
-
 Omni-Man, Invincible Wiki23 maio 2024
Omni-Man, Invincible Wiki23 maio 2024 -
Rifas23 maio 2024
-
 POKEMON RUN THROUGH!! Johto Almost Done And On To The Next!!23 maio 2024
POKEMON RUN THROUGH!! Johto Almost Done And On To The Next!!23 maio 2024 -
 Building Blocks, Alphabet Lore23 maio 2024
Building Blocks, Alphabet Lore23 maio 2024 -
Yu-Gi-Oh! TCG - 2 Player Starter Set23 maio 2024
-
 Rockstar Careers on X: Meet some of the talented #womenbehindthegames from Rockstar North and join us this #internationalwomensday in celebrating all the amazing women working in game development. Follow @rockstarcareers to see23 maio 2024
Rockstar Careers on X: Meet some of the talented #womenbehindthegames from Rockstar North and join us this #internationalwomensday in celebrating all the amazing women working in game development. Follow @rockstarcareers to see23 maio 2024 -
 Boruto: Two Blue Vortex capítulo 81 - disponível e grátis; leia agora : r/MeUGamer23 maio 2024
Boruto: Two Blue Vortex capítulo 81 - disponível e grátis; leia agora : r/MeUGamer23 maio 2024 -
 Jogo de Cozinha Crochê Elo7 Produtos Especiais23 maio 2024
Jogo de Cozinha Crochê Elo7 Produtos Especiais23 maio 2024 -
 Como desenhar um cavalo FACIL passo a passo para crianças e iniciantes 423 maio 2024
Como desenhar um cavalo FACIL passo a passo para crianças e iniciantes 423 maio 2024 -
Mladost Lucani x Radnik Surdulica 31/07/2023 na Super Liga 2023/2423 maio 2024



