AiTM/ MFA phishing attacks in combination with new Microsoft protections (2023 edition)
Por um escritor misterioso
Last updated 27 maio 2024
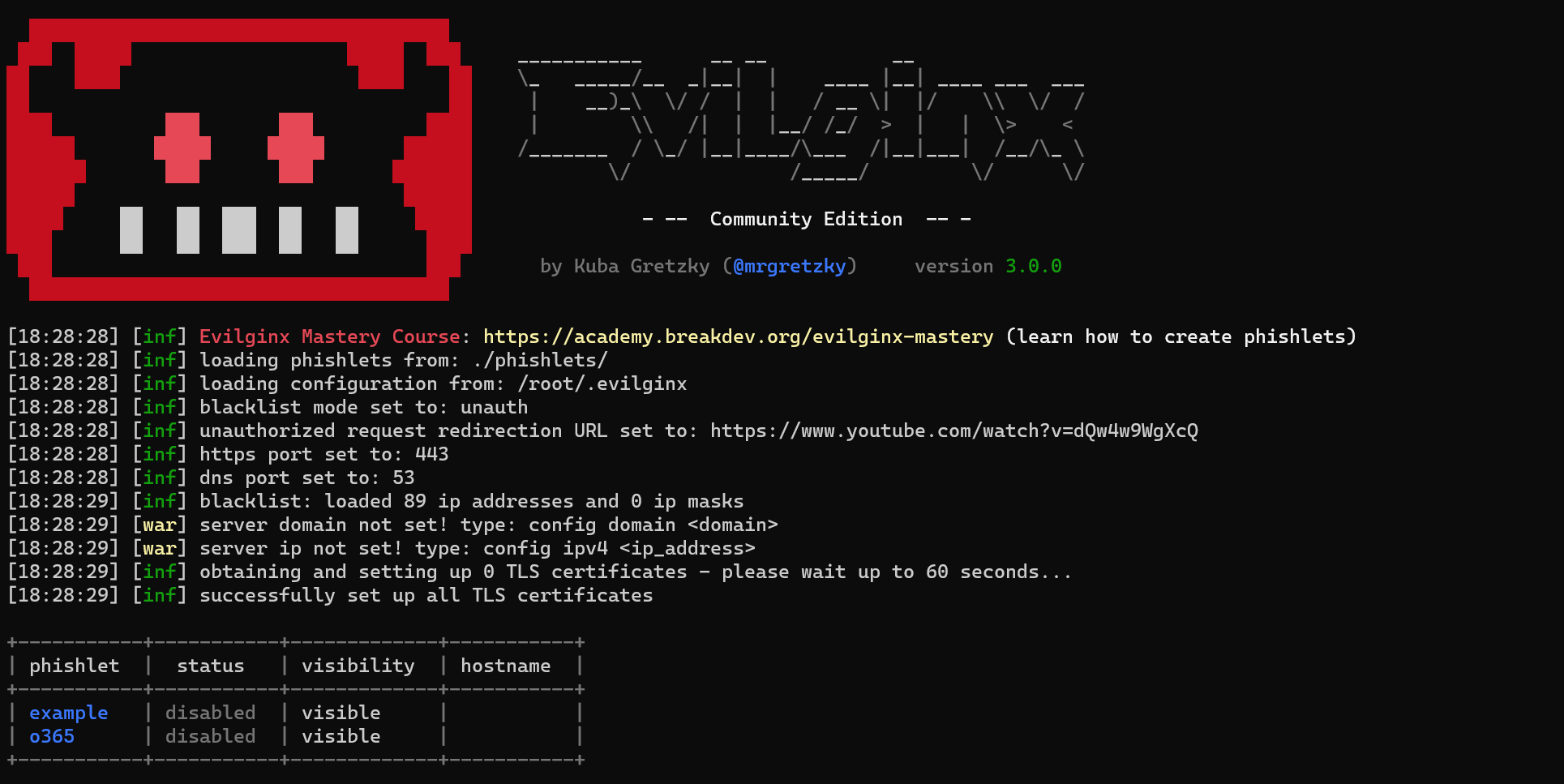
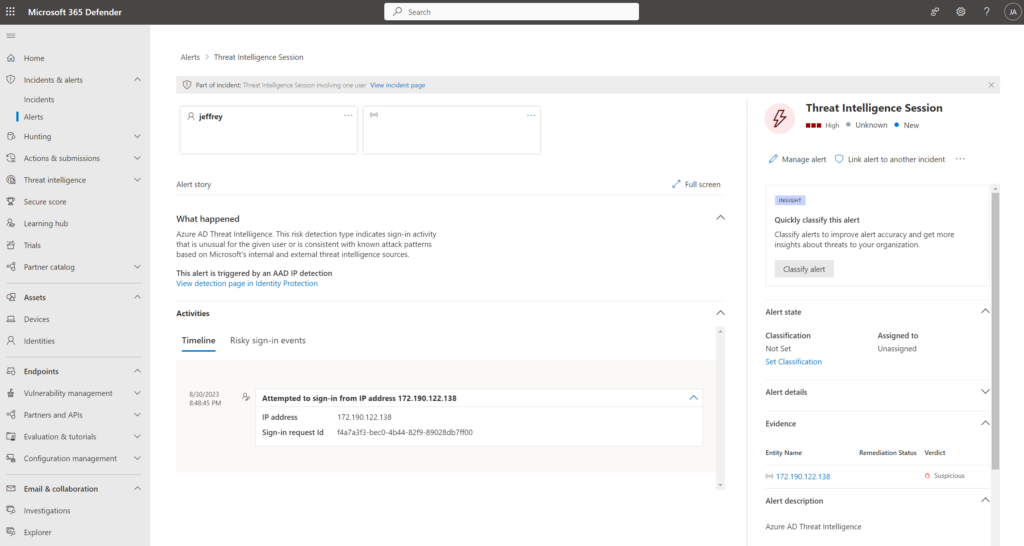
Adversary-in-the-middle phishing attacks are still more common in use. Since the removal of basic authentication from Exchange Online more and more attackers are using more modern attacks like adversary-in-the-middle phishing, cookie theft, and other used attacks. Last year I blogged about several modern
AiTM/ MFA phishing attacks in combination with new Microsoft protections (2023 edition)

Detecting and mitigating a multi-stage AiTM phishing and BEC campaign

All Attacks Are Hybrid Attacks–And What To Do About It by Vectra
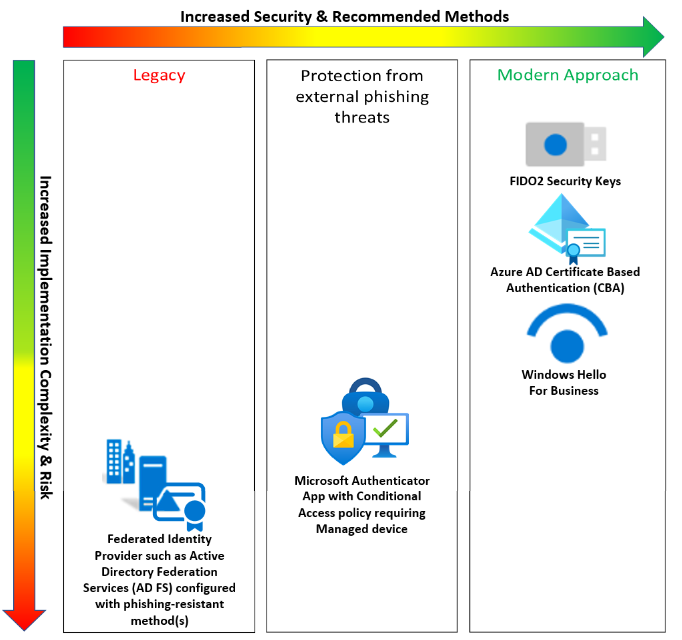
Memo 22-09 multifactor authentication requirements overview - Microsoft Entra

Jeffrey Appel on LinkedIn: How to protect Azure storage accounts (Blob) using Defender for Storage

What Is An Adversary-in-The-Middle Attack (AiTM)?

Adversary-in-the-Middle (AiTM) phishing attack: Key tactics and defense strategies

W3LL oiled machine: Group-IB uncovers covert BEC phishing empire targeting Microsoft 365 – report
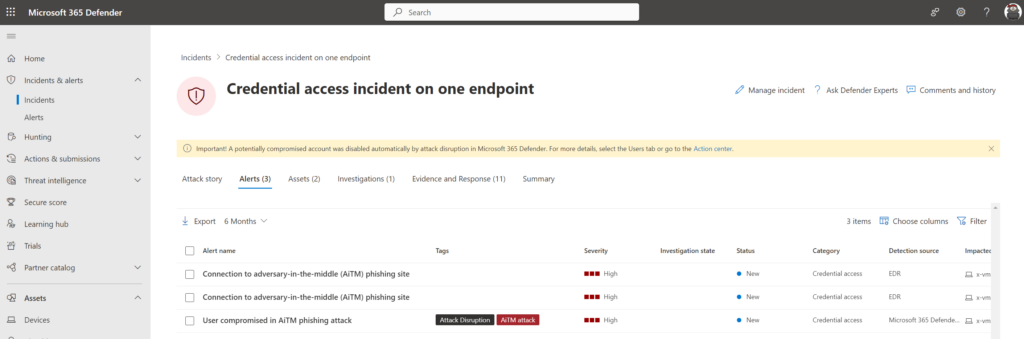
AiTM/ MFA phishing attacks in combination with new Microsoft protections (2023 edition)

What is AiTM (adversary-in-the-middle)? - Ericom Software

From cookie theft to BEC: Attackers use AiTM phishing sites as entry point to further financial fraud

Detecting and mitigating a multi-stage AiTM phishing and BEC campaign
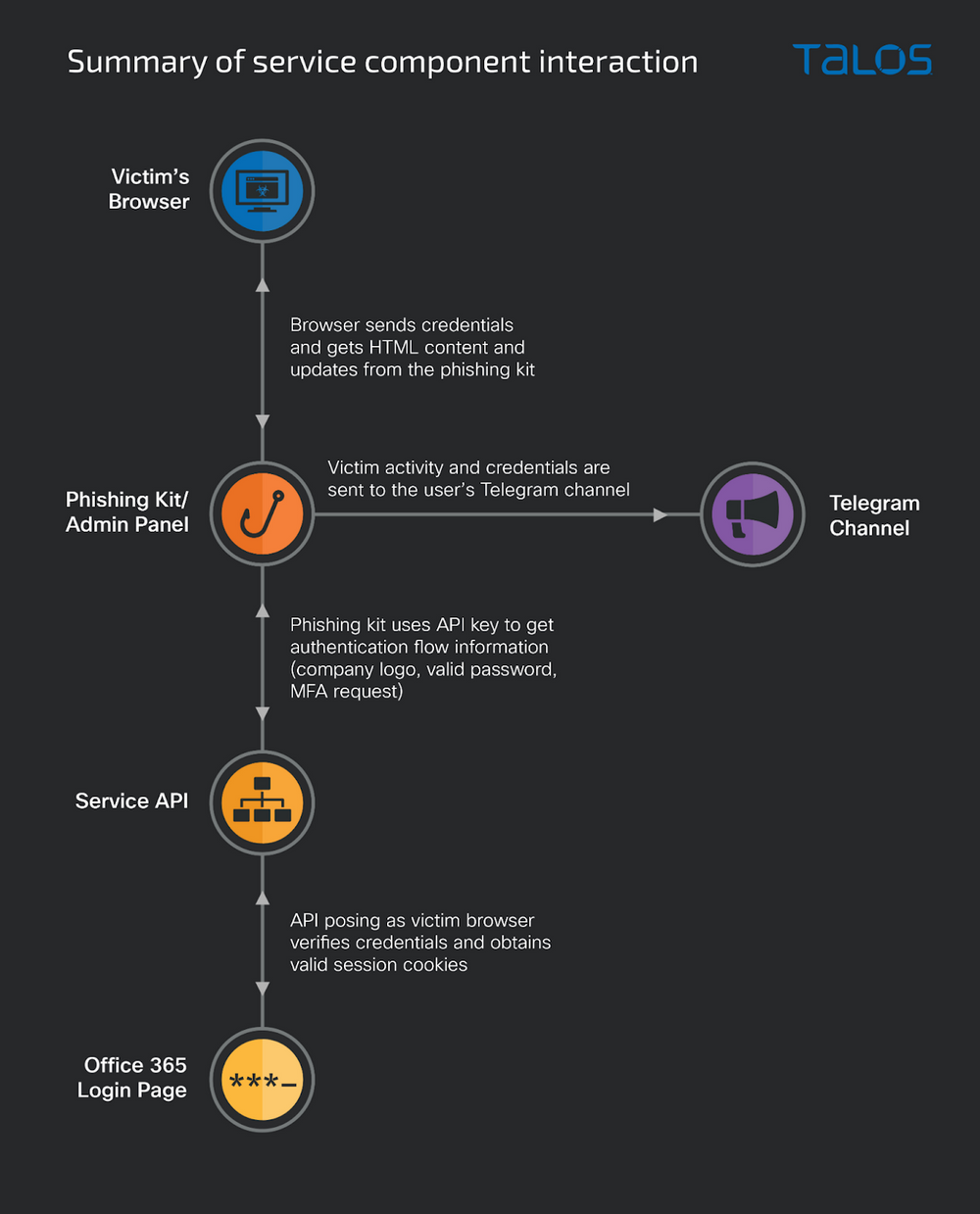
Phishing as a service continues to plague business users - SiliconANGLE

Detecting and mitigating a multi-stage AiTM phishing and BEC campaign

Microsoft Details Phishing Campaign Targeting Over 10,000 Organizations
Recomendado para você
-
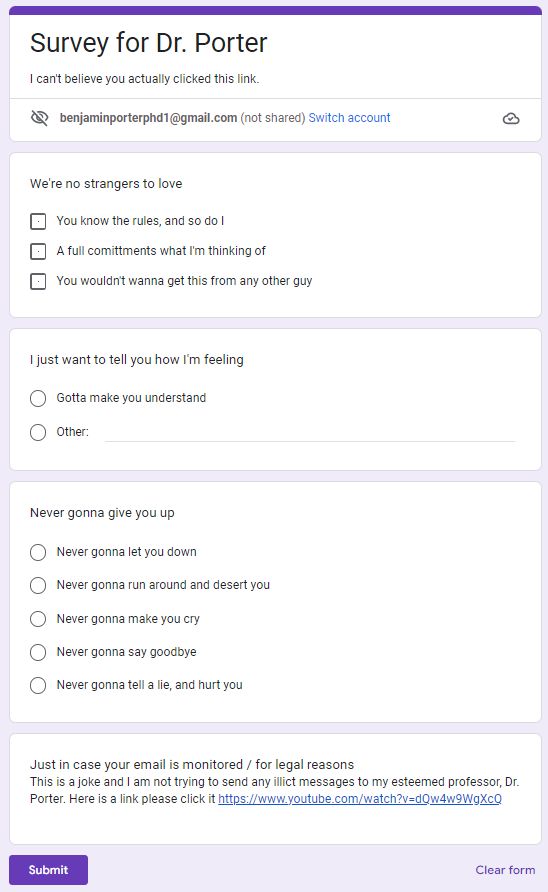
How to Rick Roll (not smart) people using a fake link27 maio 2024
-
 Grandma, Cookie Clicker Wiki27 maio 2024
Grandma, Cookie Clicker Wiki27 maio 2024 -
 COOKIE CLICKER - Beware The Grandma27 maio 2024
COOKIE CLICKER - Beware The Grandma27 maio 2024 -
The --cookies-from-browser command results in `WARNING: failed to decrypt cookie because UTF-8 decoding failed. Possibly the key is wrong?` · Issue #1073 · yt-dlp/yt-dlp · GitHub27 maio 2024
-
 Upload Data - Roboflow Docs27 maio 2024
Upload Data - Roboflow Docs27 maio 2024 -
 Abusing XSS to bypass OPT, CTF. *** Series on web hacking *****, by Tomato, Nov, 202327 maio 2024
Abusing XSS to bypass OPT, CTF. *** Series on web hacking *****, by Tomato, Nov, 202327 maio 2024 -
Rogelio M. Armino - Systems Engineer - Medical - Texas Instruments27 maio 2024
-
The Desktop - Skymods27 maio 2024
-
 Setting up and using smart links in Sell – Zendesk help27 maio 2024
Setting up and using smart links in Sell – Zendesk help27 maio 2024 -
 Gacha Cookie DailyPotato Amino Amino27 maio 2024
Gacha Cookie DailyPotato Amino Amino27 maio 2024
você pode gostar
-
 KOS-MOS - Xenoblade Chronicles 2 Guide - IGN27 maio 2024
KOS-MOS - Xenoblade Chronicles 2 Guide - IGN27 maio 2024 -
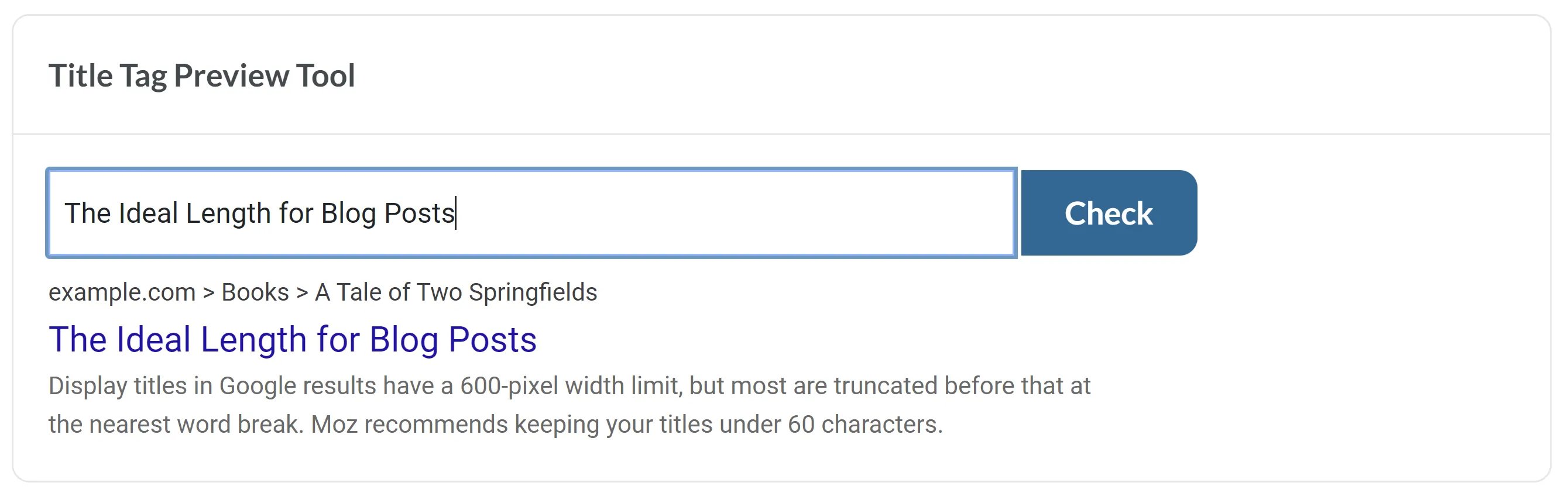 The Ideal Length for Instagram, Facebook, Twitter, & LinkedIn Posts27 maio 2024
The Ideal Length for Instagram, Facebook, Twitter, & LinkedIn Posts27 maio 2024 -
Angry Munci + Cootie =27 maio 2024
-
 M3TaLHeaD's Profile27 maio 2024
M3TaLHeaD's Profile27 maio 2024 -
BloxLand for Android - Free App Download27 maio 2024
-
gente esse jogo já tá programado pra c perder, pode ter certeza27 maio 2024
-
 Ornamento calvo do feriado do cavalo da cara27 maio 2024
Ornamento calvo do feriado do cavalo da cara27 maio 2024 -
How to Make Alchemist in Little Alchemy 2?27 maio 2024
-
 God of War II - ps2 - Walkthrough and Guide - Page 1 - GameSpy27 maio 2024
God of War II - ps2 - Walkthrough and Guide - Page 1 - GameSpy27 maio 2024 -
:max_bytes(150000):strip_icc()/69c-4a_2880x1620_r_crop-2000-3f22f7cbef9a49078530f39d9b3abe19.jpg) Maze Runner: The Death Cure review: A B-movie with an A+ budget: EW review27 maio 2024
Maze Runner: The Death Cure review: A B-movie with an A+ budget: EW review27 maio 2024